zero-risk technology review

Breaking Through Telecom Sludge: How Abilita Helps You Cut Through the Frustration
If you’ve ever tried to cancel a telecom service, dispute a billing error, or simply...

Is Cybersecurity consolidation in your future?
It is certainly no secret that cybersecurity issues are of prime importance to all stakeholders...

Selecting the right service for POTS replacement.
Over the last few years, numerous articles and white papers have been published concerning the...

Pen Testing: Key to Network Security Success
Penetration testing (pen testing) is a cybersecurity practice in which authorized professionals simulate cyberattacks on...

Secure Your High Impact IT/Telecom Business Solutions with Professional Support
Many organizations are left struggling when they are required to execute IT/Telecom projects within organizations...
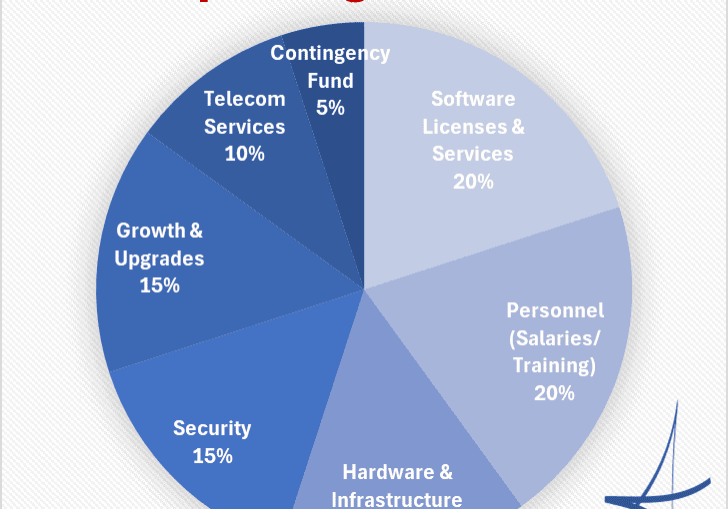
Master IT & Telecom Budgeting for 2025 Success
Many companies use this time of year to start budgeting and planning for the upcoming...

The Importance of NIST Cybersecurity Framework Compliance
Did you know? 85% of cybersecurity breaches are caused by human error. 94% of all...

The Pitfalls of the “New” Cloud Model: What You Need to Know
As cloud services continue to evolve, many companies are adopting a "new" cloud model that...

